Platform How HYPR Authenticate Works
How HYPR Passwordless Authentication Works
HYPR Authenticate: Phishing-resistant, passwordless authentication built on passkeys.
Phishing-Resistant Authentication
Eliminate credential phishing, push bombing and other credential attacks
Simple, Fast
User Experience
Authenticate once, access anything — cut down multiple logins to a single user action
Enterprise-Wide Interoperability
Deploy passkeys across your systems, IdPs and applications, for employees and customers
Independently Verified to Deliver 324% ROI
Reduce help desk and attack response costs and accelerate digital transformation
How HYPR Authenticate Phishing-Resistant MFA Works
HYPR Authenticate transforms your smartphone into a FIDO2 passkey, replacing passwords and shared secrets with secure public key cryptography. With HYPR, drastically reduce your attack surface while making login faster and simpler for your employees and customers.


How the Login Process Works
- The user initiates login to their desktop, SSO provider or connected app and HYPR challenges the user to login with their registered device.
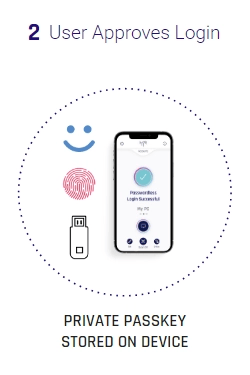
- HYPR requests the identification factors set up with their registered device and the user provides their chosen verification factor, such as a TouchID. HYPR also supports hardware options such as YubiKeys.
- This unlocks the private passkey, which is used to sign the challenge. It’s matched against the corresponding public key.
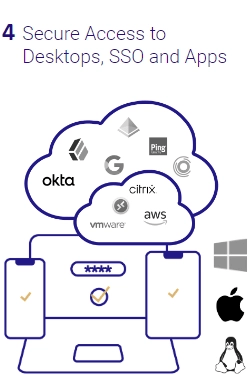
- The user is logged into their desktop, corporate single sign-on services, and all downstream apps.
What You Experience
This all happens in a single, fast authentication flow. For example, on an iPhone with FaceID, you tap the HYPR Authenticate app, look at your phone, and you’re in.
If you already signed into your desktop using HYPR, then the verified identity is automatically passed to the SSO, no additional verification steps unless step-up authentication is required.
Passkey-Based Authentication Plus Much More
Passkeys are the means but not the end. HYPR's passwordless solution provides a full Identity Assurance ecosystem to securely and seamlessly accelerate business for the modern enterprise.
Full-Featured Platform
HYPR incorporates both standard synced passkeys and device-bound HYPR Enterprise Passkeys into a comprehensive, enterprise-ready Identity Assurance platform.


Identity Solutions For Your Workforce
Protect your entire workforce — onsite, remote and contractors — while reducing friction. HYPR’s easy-to-use, passkey-based MFA, continuous risk monitoring, and adaptive verification designed for KYE deliver comprehensive identity security and usability.
Identity Solutions For Your Customers
Watch customer satisfaction (CSAT) skyrocket while protecting against account takeover and fraud. HYPR's passkey-based MFA removes friction and ensures you meet strong customer authentication requirements (SCA). Proactive risk controls and integrated identity verification provide end to end identity protection.
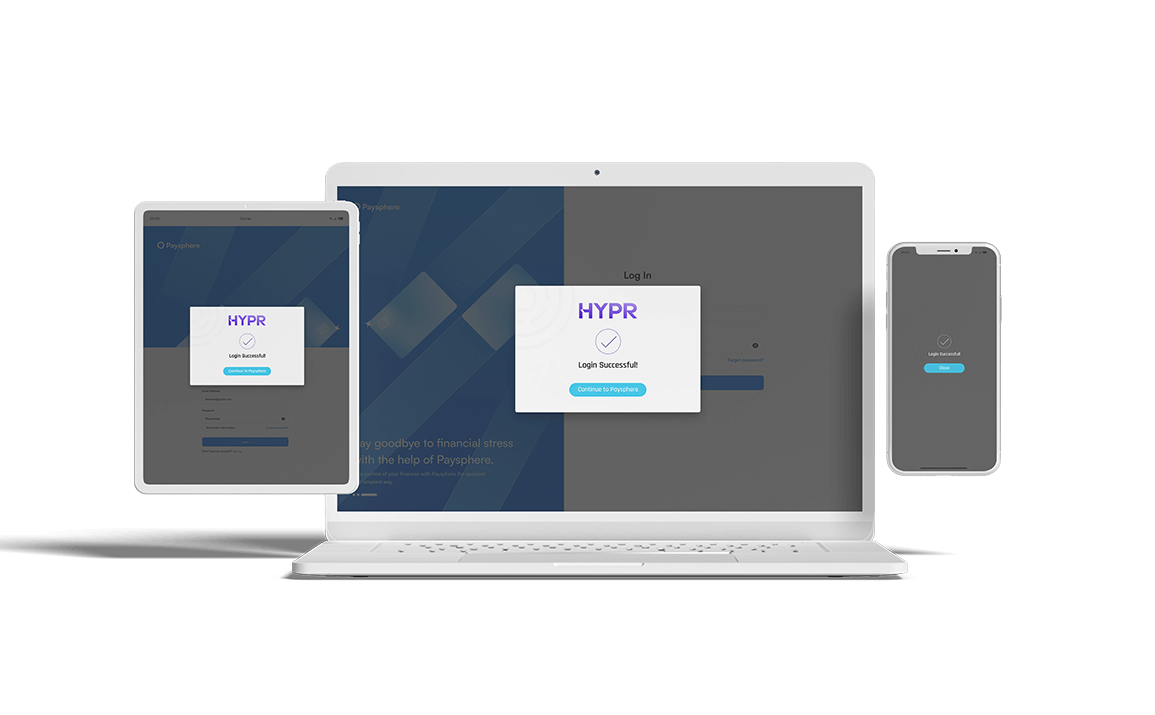

Coverage Desktop to Cloud
HYPR replaces passwords with passkeys in all aspects of your environment, securing and unifying authentication across all your devices, applications and platforms.
What Are the Top Considerations When Going Passwordless?
It's critical to find the passwordless solution that best fits the needs and requirements of your organization. Look at these key areas.
Discover the 12 Essential Considerations for Passwordless.

Request a Demo
Experience passwordless MFA that secures and empowers your business. See what identity verification built for the workforce looks like. Learn how comprehensive Identity Assurance protects the entire identity lifecycle.
Fill out the form to get a demo from an identity security expert, customized around your organization’s environment and needs.